
Back on Track, Malware Cleaned
Dear Readers,
We are back on track after cleaning a malware infection on our website. The warnings at google search and Firefox browser will take a day or to go away.
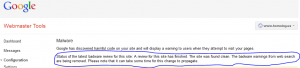
Here are the details on what we discovered so far on this type of attack so that others can benefit.
The malware/attack we faced is called ‘base64_decode injection attack’. What
happens for hacked websites? One fine morning, the webmaster opens the server
side files and finds that every single php file has an extra line in front of
it. It starts with php prompt and then
eval(base64_decode("aWYoZnVuY3Rpb25fZXhpc3RzKCdvYl9zdG...... [a huge 7000
character line that ends with ?–>] and then your original code follows. Every
single php file has the same line injected in it.
At this point, all script gurus are probably thinking about how to write a cool script that removes all those extra lines from each php file, and let the site be back in action.
** THAT IS A BAD SOLUTION.**
Why? It is because for the above kind of attack, the actual malware infection to your website likely happened long before the base64_decode injection. Usually, a short and harmless-looking backdoor code hides among your scripts for a while, and then gets activated by some external website. If you do not remove that activation script from your web server files, the attack will happen again within one to two weeks. Typically, the original code enters the website through one or other wordpress plugins. Wordpress, by itself, is very secure, but the same cannot be said about all plugins developed by various users.
For our website, we cleaned our webserver by deleting all existing codes and then installed everything (wordpress, SMF, etc.) from scratch from their original sources. We also inspected all scripts written by us to make sure they do not have any malware. Finally, we deactivated all wordpress plugins for the time being. Hopefully, that will keep us safe for a while.
In the meanwhile, we are going through the backup of our infected website to learn how the base64_decode injected started. Here are bits and pieces of information that may help you, if your website gets attacked in the same manner.
A. The injected line ('
eval(base64_decode("aWYoZnVuY3Rpb25fZXhpc3RzKCdvYl9zdG......') is a php code
written in encoded manner so that nobody can easily figure out what it does by
merely looking into it. The only way to understand the code is to paste the
long line into a base64 decoder. Someone else
already did that hard work for our infected code, and posted it here
online.
B. If you go through the code, you will see that it has another round of base64_decode within it. That is where the names of three websites are hidden . The first one (‘http://ens122zzzddazz.com/’) is possibly a fake lead, whereas the second and third ones are right one. However, you will also find that the second and third ones vary in their various reincarnations. The hackers are constantly shifting the base of their operation to stay unrecognized. We found that the second and the third ones are always from Russian domains.
C. Few bloggers did extensive research on how to fix your website and what the attack codes are likely doing. Here are relevant links.
Four part series (posting links for the first and the fourth) -
recovering from base64 wordpress hack part 1
tales from a base64 wordpress hack part 4 dissection
Other useful links:
wordpress injection attack - link1
wordpress injection attack - link2
wordpress injection attack - link3
wordpress injection attack - link4
One useful tip - please go through the comment sections in the above links for lot of valuable information.